Safari 浏览器和iOS应用程序将永久cookie保存在Cookies.binarycookies文件中。这于其他桌面浏览器的保存方式是不同的。例如IE会将永久cookie以文本的方式保存在Temporary 临时文件夹下,Firefox 和chrome则会将永久cookie保存在一个sqlite数据库中。保存在数据库中和文本中的cookie是非常容易读取的。但是并没有合适的工具来从Cookies.binarycookies二进制文件中读取cookies信息。所以我写了一个python脚本(BinaryCookieReader.py)来获取Cookies.binarycookies文件中所有的cookie信息,这个脚本的输入参数为Cookies.binarycookies文件。
使用方法:
1. 下载并且安装 Python
2. 将python的路径添加到系统的PATH环境变量中
3. 下载 BinaryCookieReader.py
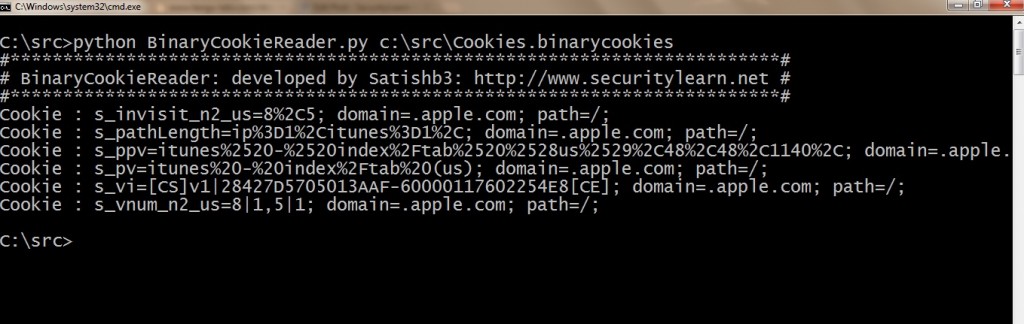
4. 打开命令提示符并且输入下面的命令。它将会从Cookies.binarycookies文件中解析出所有的cookie
Python BinaryCookieReader.py [Cookie.binarycookies-file-path]