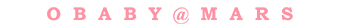Affinic Debugger GUI, aka. ADG, uses multiple document interface(MDI) design so that it can open multiple source viewers and one assembly code viewer. The surrounding docking widgets are fully movable and provides various functionality. They are console, stack, breakpoint, source list, watch, register and command pool widgets.
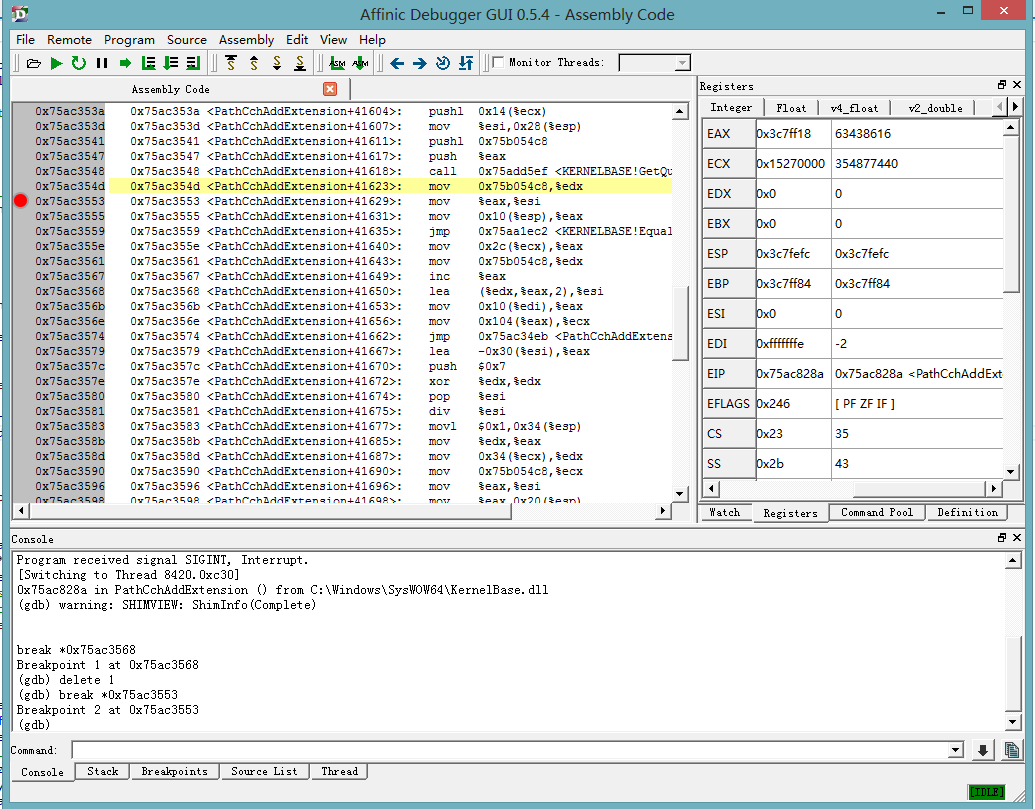
Web Albums(iPhone) 的蛋疼明文密码
一款蛮不错的的Picasa相册同步软件,并且还有个密码保护功能,看起来很帅的样子。设置密码之后习惯性的想看下密码保存在什么地方,是不是明文的,于是随便在文件夹下翻了翻,不小心就找到了。娃哈哈,蛋疼啊,如果忘记密码了去软件目录下找到这个文件:
/var/mobile/Applications/51AE867E-C284-4961-B6D6-48428404FE12/Library/Preferences/com.yourcompany.PhotoGator.plist
All In One OllyDBG Tools Pack
AIO OllyDBG Tools Pack
============================================
uploader : [belajar-cracking.blogspot]
============================================
All tools for ollyDBG v1.10 / v2.0. And ImmunityDBG. Contain plugins, script, patch, extra tools, utilities etc. I hope you like it… 
Book Publisher Wanted!(寻求图书出版商)
DeIDA Package 1.4
DeDe is Excellent Delphi program analyzing tool, but I still prefer IDA for
navigation & documentation.Exe-2-Dpr is another very useful utility (and also work with old 16-bit Delphi
programs).I always look for way to grab as many info from this great program’s output as
possible. So, I wrote a few stupid progs just to _reformate_ Exe2dpr & DeDe
output and import into IDA by simple IDC script.That’s all.
How to use:
———–
EDM:
> -*- EDM 1.4 * Copyright (c) Aleph 2001-2003 -*-
> Exe-2-Dpr output files reformatter
> Usage: edm.com [> ProjectName.DDM]
Apply exe2dpr.exe to analyzed proggy. Place all exe2dpr output in some
directory. Now, run edm.com in this directory and redirect edm output to some
file. edm will be scan all *.pas files in the directory and create output file
in *.ddm format. Use deida.idc script for import the *.ddm file to IDA database.
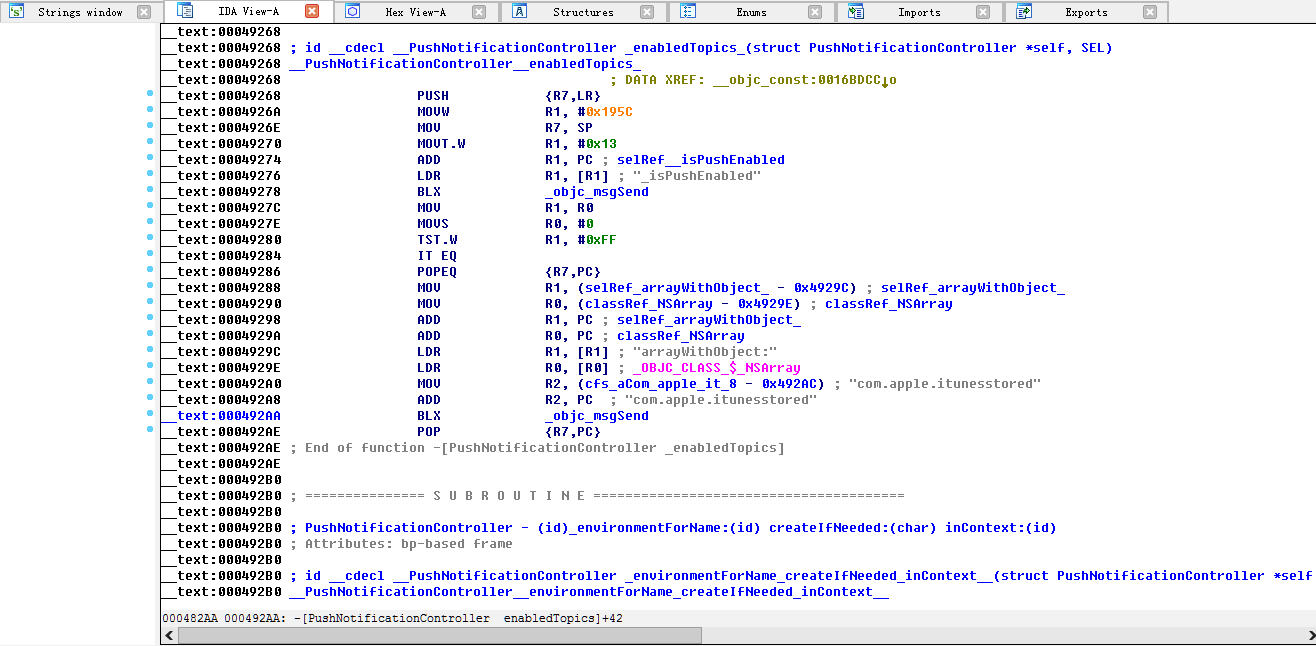
fixobjc idc script for IDA Pro
This is an attempt to improve the original fixobjc.idc script by Willem Jan Hengeveld.
For now it’s only compatible with Mach-O 32bits binaries for Mac OS X.
My goal is to make it compatible with all Mac OS X and iOS binaries.
fG!